Principles of the Zero Trust Model
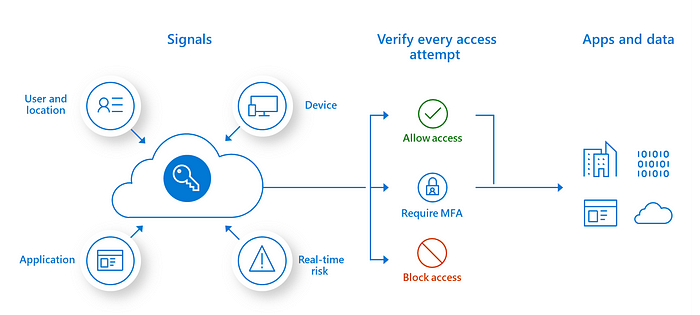
The Zero Trust Model is a security model that is designed to ensure the security of enterprise networks, data, and applications. It is based on the principle of “never trust, always verify” and assumes that all users, devices, and applications are potential threats.
This means that access to resources is granted only after verifying the identity and trustworthiness of the user, device, or application.
Recommended: How to Have “Security Nightmare-Free” Application Modernization?
In this article, we will discuss the principles of the Zero Trust Model and how they can be implemented to ensure the security of enterprise networks.
Principle 1: Verify explicitly
The first principle of the Zero Trust Model is to “verify explicitly”. This means that access to resources should be granted only after verifying the identity and trustworthiness of the user, device, or application. This is in contrast to the traditional security model, which assumes that everything inside the network is trusted.
To implement this principle, organizations should implement strong authentication mechanisms such as multi-factor authentication and biometric authentication. Additionally, they should implement authorization policies that restrict access based on the user’s role, device type, and location. Access should be granted only when the user, device, or application is explicitly authenticated and authorized.
Principle 2: Use least privilege access
The second principle of the Zero Trust Model is to “use least privilege access”. This means that users should be granted only the minimum access required to perform their job. This is in contrast to the traditional security model, which grants users broad access to resources based on their job function.
To implement this principle, organizations should implement access control policies that restrict access based on the principle of least privilege. Access should be granted only to the resources that are required to perform the job function. Additionally, access should be revoked when the user’s job function changes, or when the user leaves the organization.
Principle 3: Assume breach
The third principle of the Zero Trust Model is to “assume breach”. This means that organizations should assume that all users, devices, and applications are potentially compromised. This is in contrast to the traditional security model, which assumes that everything inside the network is trusted.
To implement this principle, organizations should implement monitoring and detection mechanisms that can detect and respond to potential breaches. This includes implementing intrusion detection systems (IDS), security information and event management (SIEM) systems, and endpoint detection and response (EDR) systems.
Additionally, organizations should implement incident response plans that can help them respond to security incidents quickly and effectively.
Principle 4: Segment network access
The fourth principle of the Zero Trust Model is to “segment network access”. This means that organizations should divide their network into smaller segments and restrict access between them. This is in contrast to the traditional security model, which assumes that everything inside the network is trusted.
To implement this principle, organizations should implement network segmentation policies that restrict access between different network segments. This can be achieved by implementing firewalls, virtual private networks (VPNs), and other network access control mechanisms.
Additionally, organizations should implement policies that restrict the movement of data between different network segments.
Principle 5: Inspect and log traffic
The fifth principle of the Zero Trust Model is to “inspect and log traffic”. This means that organizations should inspect all traffic entering and leaving the network and log all traffic for analysis. This is in contrast to the traditional security model, which assumes that everything inside the network is trusted.
To implement this principle, organizations should implement network traffic analysis tools that can inspect all traffic entering and leaving the network. Additionally, organizations should implement logging mechanisms that can record all network traffic for analysis. This can help organizations detect and respond to security incidents quickly and effectively.
In conclusion, the Zero Trust Model is a security model that is designed to ensure the security of enterprise networks, data, and applications. It is based on the principle of “never trust, always verify” and assumes that all users, devices, and applications are potential threats.
The principles of the Zero Trust Model — verify explicitly, use least privilege access, assume breach, segment network access, and inspect and log traffic — provide a comprehensive security framework that can help organizations protect their networks from security threats.
By implementing these principles, organizations can ensure that their networks are secure, their data is protected, and their applications are safe from potential security breaches.